SYGNIA - MILITARY GRADE CYBER SECURITY
Elite Consulting & Incident Response
Industry leading Cybersecurity technologies
We only work with Industry leading Cybersecurity technologies. We do the leg work so you don't have to.
Cybersecurity Knowledge
The team at Witz Cybersecurity has a long history in complex Cybersecurity technologies and IT related security issues.
Consulting Service
We consult with companies to protect their clients' digital systems and DATA from cyber threats.
Continuous Cybersecurity Posture Monitoring
Elite Incident Response & Consulting
Secure All Mobile Devices
Technology Partners
Witz Cybersecurity’s range of unique, disruptive and innovative technologies provides you with the next level of Cyber protection. If you would like a demo or further information, please email us at support@witzcybersecurity.com

Real-time threat detection and response
A comprehensive and customizable cybersecurity platform that provides real-time threat detection and response, deep visibility into an organization's IT environment, and comprehensive vulnerability management solutions.
Detection and Monitoring
Triage and Investigation
Forensic Analysis
Incident Response
Thread Hunting

Trusted Mobile Workplace for Mobile Security
the first endpoint security solution designed to manage mobile data, not mobile devices. Employing the highest levels of data encryption and containerisation – regardless if company owned (COPE) or personally owned (BYOD) – that isolates all work-related email, apps and data from personal use on the same device. No intrusive MDM agents are required.
Single Application Installation
Security without MDM Agents
Zero Trust Endpoint Security
Data Encryption and Containerisation
End-to-End Data Loss Protection (DLP)
Compatible with Both COPE and BYOD



Automated Security Compliance platform
A cloud-native security platform that provides a unified identity and access management solution for cloud-native applications, enabling organizations to secure and control access to their distributed applications and infrastructure.
How Scytale AI reduces the burden of compliance:
Integrations
Automations
Workflows
Compliance Experts
The steps with Scytale AI:
Onboard your company
Add stakeholders
Integrate your tech
Complete tasks
Pass audit

World's first AI Phishing simulator
Introducing the AI Phishing Simulation Builder, a powerful tool that revolutionizes the world of cybersecurity training. With this innovative platform, users can effortlessly generate custom phishing simulations, complete with a phishing email, a convincing phishing landing page, and an insightful micro training.
Cywareness New Features
Improved Export Process: Exporting data is now faster and more efficient! Timestamps have been added to simulation user interactions, streamlining data management.
Enhanced Wizard Power: Empower your training initiatives with our enhanced wizard, now available for both video training and simulations. This feature unlocks new possibilities for your training strategies.
AI Phishing Simulation Builder, a powerful tool that revolutionizes the world of cybersecurity training
Automatic Performance Report: Get analytics of each simulated attack, from opening an email to inserting data into our phishing page.
Cywareness allows you to analyse the performance of each employee, team, department, or even a specific office.

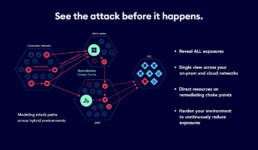
Close today's exposures, prevent tomorrow's attacks
XM Cyber is transforming the way organizations find and fix security exposures across the hybrid cloud. See how attackers leverage and combine misconfigurations, vulnerabilities, identity exposures, and more, across your AWS, Azure, GCP and on-prem environments to compromise your critical assets. With XM Cyber, you can see all the ways attackers might go, and all the best ways to stop them, with a fraction of the effort.
Continuous risk visibility
Safe automated monitoring of entire network
Comprehensive attack modelling from any breach point to critical assets
Proactive security to rapidly prioritize and respond to risk
Hybrid coverage across on-prem and multi- cloud in a single view
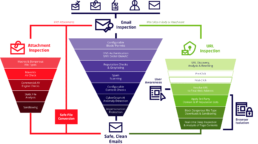
Email Security Protection against Cyber-attacks
One of the best email security solutions protecting Government, Law enforcement, legal and financial institutions to name only a few verticals.
Prevention of business email compromise, phishing, and spear-phishing
Neutralization of malicious URLs, attachments, spam and malware
Protection for employees – both in the office and remotely